Today, our world is connected in ways which were unimaginable a generation ago. We take for granted the ability to communicate in real time, across the world using both audio and video. In recent times it is possible for anyone to become a published author or to create their own TV channel with the click of a button. All of this is possible due to advances in how we connect computers together, called networking.
Networks have evolved rapidly in the last 20 years, with huge leaps in not only the speed of communication but also wireless technologies that are now so ubiquitous in our lives. Networks are often greatly misunderstood, however their underlying technology almost directly mirrors the world around us making it easy to understand with some explanation.
In this section (click to jump):
What is a Network?
At its most basic, a network is any two or more things that are connected together in some way. You are surrounded by them – the roads, railways, postal service, phone and even your friendship group are all examples of networks, things that have been connected together.
In computing we have a really clear definition for what a network is:
Network – two or more devices (nodes) connected together for the purpose of sharing data and communication.
Notice the word “node” in our definition. A node is simply a point or device which is connected to a network. We use this word because networks are made up of a vast and varied mixture of computing hardware as you will see later when learning about network hardware. A node could be anything – a computer, printer, smart speaker, switch, router, server… The list is almost endless.
Networks exist for two clear purposes:
- To enable the sharing of data (files) and resources – things like printers or servers.
- To enable communication
For all of this to happen, something quite incredible has taken place – the whole world has decided to effectively “speak the same language.” For a network to operate, every single device regardless of manufacturer, model or features must communicate in exactly the same way.
There are rules for how networks are operated, called “standards” and there are lots of networking standards depending on what you are trying to achieve. We look at these in much greater detail in the next section on “protocols” but for now it is sufficient to just understand that all devices, all around the world, all use the same rules for communication.
Networking has forever changed the way in which we use computers and other electronic devices. The advantages are almost endless, but a summary is below:
Advantages of networking devices together:
- It enables us to communicate (obviously) via various means such as video conferencing, email or instant messaging
- We can work collaboratively on projects
- We can share files, data and information that other people may need
- We can share expensive resources such as printers and the internet (you do this all the time on your home wireless network) which saves money.
- We can share software
- We can look after everything in one place – control the network centrally
- We can back up work all in one place – on a server
So it’s a pretty good idea, right?!
However there are one or two disadvantages you should be aware of:
- Adding computers to a network has a data security implication
- There is a cost involved – you have to buy equipment such as cables, switches and access points if you’re going wireless
- It will also cost you to install all the equipment – networking is a skilled job.
- You may need to employ an administrator to look after your network
Having said all that, the benefits of networking usually far outweigh any negatives.
We need to talk about packets
At this point we need to take a detour to understand how data is actually sent across a network. Fortunately, if you can understand how a letter goes from a postbox to its destination, you’ll have no trouble understanding how computer networks send data.
To understand how data travels in a network, let’s look at an example.
I want to make a healthy, nutritious breakfast so I go on YouTube and start streaming the latest episode of Kay’s Good Cooking. Everything is good, I’ve got plenty of lard in, plenty of tins of things to mash up together and I’m ready to knock up some serious gourmet action in my kitchen.
So how does that video make its way from YouTube to my phone or computer?
The first thing to understand is that data is not sent all at once as one big chunk. This web page was not sent to your device all at once, not even the small pictures dotted about the place. Absolutely everything that gets sent through a network ends up being broken into many little pieces first.
If you’ve ever watched Charlie and the Chocolate Factory, you’re going to get this without a problem. The way networks work is pretty much the same as Wonka Vision (click the link to see for yourself!)
Now, let’s make life easy and focus on how one single frame of the video is sent. All video works by showing still pictures, one after the other, very quickly to fool us in to thinking it’s a moving image. So, to simplify this massively, when a video is sent to your device you are actually just receiving a stream of pictures one after the other.
Here’s the frame we’re going to send:

There’s our Kay with two banging “all day” breakfasts, enough to give you furry arteries for life.
The first thing that happens is that this image is split into equal chunks:

This is done so that:
- Each piece of data sent through the network is small
- This makes it quick to send
- Most importantly, if one piece gets lost, we do not lose the entire image and we don’t have to re-send the entire image. This is a huge time saver.
To enable us to put the picture back together again at the other end, we then number each piece:

This is another top idea, because not only does it mean we know what order the pieces go in when we put it back together, it also means that we do not need to receive the data in order. If all the pieces arrive in a random order, it doesn’t matter, we just look at the numbers an put them the right way round again. Bonus.
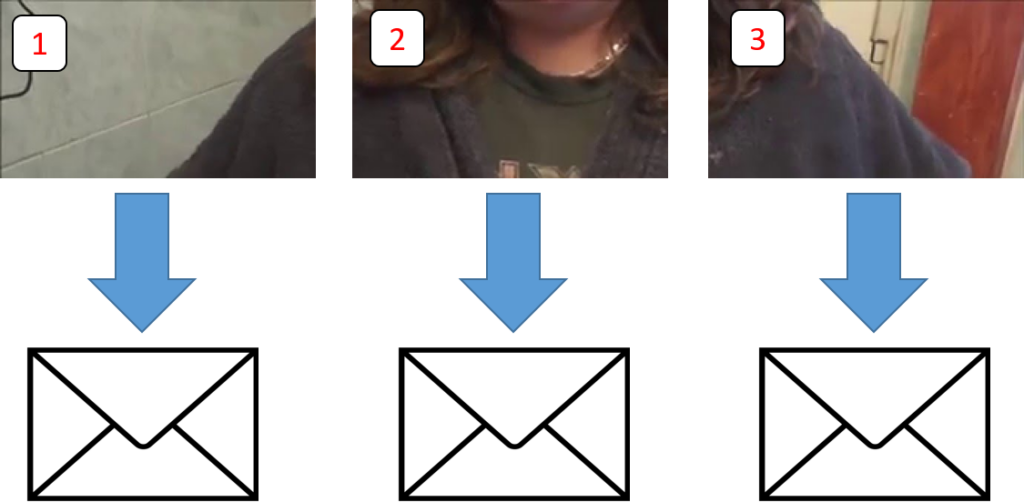
Once we’ve done all this, we package the data up to create something called a packet. If this sounds like we’re sending things through the post then… that’s because it’s almost identical. Indeed, why not go all out for a truly retro experience and have an “offline Instagram day.” Simply take and print out endless pictures of food, pets, selfies and “hilarious memes.” Then, spend an afternoon snipping pictures into thousands of pieces and then post them in individual envelopes to your friends. It should only set you back a thousand pounds or so in stamps and think of all the fun they’ll have with the sellotape when they arrive! Awesome.
Packets are the key to how data is sent through a network. Absolutely everything – web page, songs you stream, videos, apps, your latest social media update about your dinner… everything is sent as a series of packets through a network.
What does a packet contain, then? Well, just like a letter you’d send in the post, it needs some information on it to help it reach its destination.
A packet consists of:
- The actual data you are sending (in this case, a bit of a picture)
- A header containing:
- The destination address (these are IP addresses, more on those later)
- The source address (so you know where it came from)
- Some checksum/error correction data (because its a wild place out there and data can get damaged in transit and we’d like to be able to fix that if it happens)
Once the data is neatly packaged up in a packet, we can then actually send it down a wire on its way to its destination.
The job of getting a packet from one place to another is taken care of by devices called routers and switches which we look at in far greater detail later on.

Eventually, the packets will make their way to their destination and it is very likely that, as in the picture above, these packets arrive out of order. Not to worry, the receiving device simply waits until all the packets arrive and then just rearranges them in to the correct order to recreate the original data.
Should a packet not arrive, after a certain amount of time the receiving device can just ask for the packet to be sent again.
If data arrives corrupted for some reason, then the device has two options – first it can use the checksum/error correction data to try and fix the problem itself. If this fails, then it will have to ask for the packet to be sent again.
It is incredibly easy for data to become corrupted in transit, and if this happens then as we’ve just seen, it results in the data having to be sent again. Imagine if we had not split our data in to packets – you could be in the position of having to repeatedly just send and re-send a huge file over and over again until it arrives intact. The chances of this happening get smaller and smaller as the amount of data we send gets bigger. This is why packets are so important – without them your data may, quite literally, never arrive.
Packets – a summary
Data is split in to equal sized chunks before it is sent through a network.
A packet of data is one of these chunks of data, wrapped up with other data that ensures it can be delivered to its destination.
A packet contains:
- some data
- a checksum or error correction data
- the source address
- the destination address
- a packet number – x out of x (e.g. 5 of 100) so it can be put back together in the right order on arrival
- a “time to live” counter which counts how many “hops” through switches or routers it has taken and will result in the packet being discarded if this number is reached
The advantages of using packets are:
- Smaller pieces of data are less likely to be involved in collisions
- If data is corrupted or lost, then a small amount of data takes much less time to re send
- If a packet is lost it can be re-sent, rather than needing the whole file to be re-sent. This is much quicker.
- Packets may all take different routes through the network, meaning they can all take the best/most efficient path at the time they are sent. This makes efficient use of the network and enables errors/problems to be avoided (like a diversion on a road)
The disadvantages of packets are:
- Making packets and re-assembling data has an overhead (it uses processing time). This isn’t usually a problem as virtually all network cards have dedicated hardware chips that do the processing of packets instead of the main CPU.
Types of Network – LAN and WAN
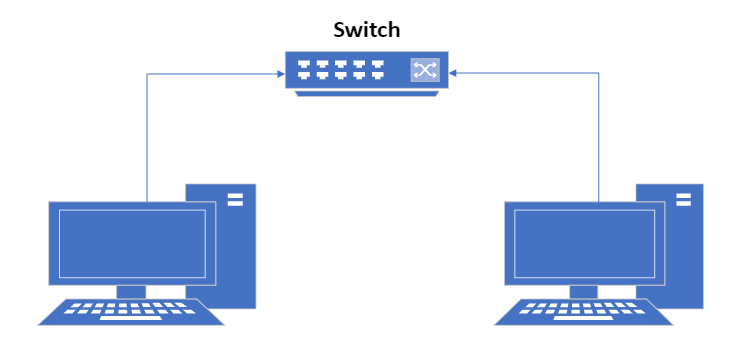
The simplest possible form of network would be two devices joined together, something like in the diagram below:
However, beyond this things quickly get large and more complicated. There is a need for us to categorise networks based on their size, location and the types of communications links they make use of. These two categories are:
- LAN or Local Area Network
- WAN or Wide Area Network
We need to look at both in more detail.
LANs
LAN stands for Local Area Network and is the term used to describe small, privately owned networks.
A LAN has some very specific characteristics that you need to know about for your exam:
- They are contained within a single building or organisation. This is often described as “confined to a small geographic area or location”
- They use dedicated, equipment and connections between devices
- They are internal networks.
- Dedicated equipment means that the company, person or organisation owns or is responsible for all equipment
- This also means that connections should be reliable and fast as they are not shared with other users/organisations
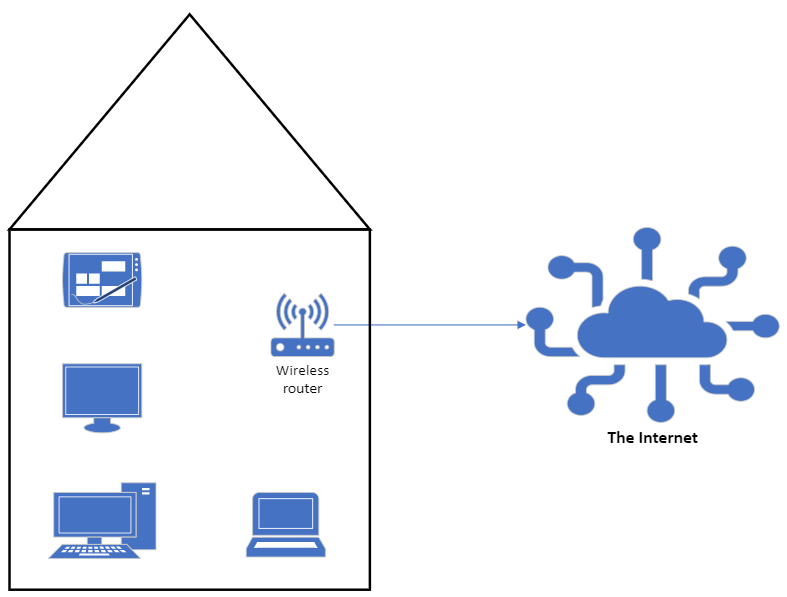
Nodes in a LAN may consist of any type of device that is capable of connecting to a network such as computers, printers, tablets and laptops. There is no limit to the number of devices in a LAN.
To create a LAN devices must be connected together using either a Switch or a Wireless Access Point (WAP). A LAN can contain any number of switches or WAP’s and the complexity of a LAN can vary massively depending on the number of devices connected together.
One thing you must note is that a LAN is not “the internet.” This is a very common mistake and at no point should you mention the internet when talking about a LAN. Not yet, anyway.
LAN’s are restricted in their geographic spread or size to one small area or organisation. This can be anything from a single room to a university which may have multiple buildings all with lots of equipment connected together to form a network. They are both LAN’s despite the obvious size difference because they are both privately owned, contained to one organisation and cover a small geographic area.
How do you know when a LAN stops being a LAN? The answer is as soon as you connect it to the internet using a Router. Everything after the Router is then no longer part of an internal, private network and therefore is not part of a LAN. We will look at Routers in more detail later.
To summarise:
- LAN stands for Local Area Network
- They are confined to one geographic location or organisation
- They make use of dedicated equipment – it is not shared with other individuals or organisations
- As a consequence, data transfer is usually quick and reliable
- A LAN can contain any type of device and any number of them
- LAN’s are not the Internet!
- To connect a LAN to the internet a Router is required, everything after the router is not part of a LAN
WANs
WAN stands for Wide Area Network and is the term used to describe any network where connected devices are geographically remote (far apart) from each other. The clearest example of this is the Internet.
Our definition for the exam is as follows:
WAN: A network covering a large geographic area, usually connected using shared, leased or other external communication equipment.
Network experts get really upset by our definition of a WAN and that’s because we’re keeping things simple for the purpose of your GCSE. In reality there is a need to differentiate between networks of different sizes and characteristics, but fortunately for us we ignore all this and simply say that any network which is larger than a LAN is a WAN. That’s nice, isn’t it?
WAN’s are characterised by their size – they cover large areas and that can mean anything from a town or city to the entire world in the case of the internet (you can see why we’re upsetting the network beards.) WAN’s may also consist of many smaller networks that have been connected together, usually via routers.
Moreover, WAN’s don’t use dedicated connections to each device and therefore we find that traffic on any given connection is usually shared amongst many different users. The easiest way to understand this is your home internet connection.
Inside your house LAN, everything is owned by you, only you and your devices are making use of the connections available. You are connected to the outside world via your internet connection – this is literally a cable that you rent from your internet provider (Virgin, BT, Sky, Zen etc.) Your home router and this cable connects you to a WAN and it won’t come as a surprise that you don’t own this equipment, nor do you own any of the cables your data travels down to get to the various servers that your Netflix content is located on, for example. These cables, routers, switches and servers are all owned by different companies and the connections to them are all shared by many, many thousands of other internet users.
This leads us to the following summary of WAN’s:
- They cover a large geographic area
- Devices are geographically remote
- Makes use of shared, leased or rented connections and equipment
- Performance may be variable due to these shared connections
- You do not own nor control all of the equipment in a WAN
- The biggest example of a WAN is the internet
Network Topologies
Once a network grows beyond a handful of devices it quickly starts to become quite complex. Networks of any reasonable size require careful design and planning to ensure they work efficiently, respond quickly and don’t degrade in performance as more users or devices are added to the network.
One of the most important decisions a network designer will make is the topology to be used. Topology means “how elements in a network are related” and is simply a word used to describe how things are connected together in a network.
There are various different network topologies and designs which are used in the real world. Often, these can even be mixed together where we need reliability or where budget does not allow for more robust design. For your GCSE you need to know about the star and mesh topologies.
Star
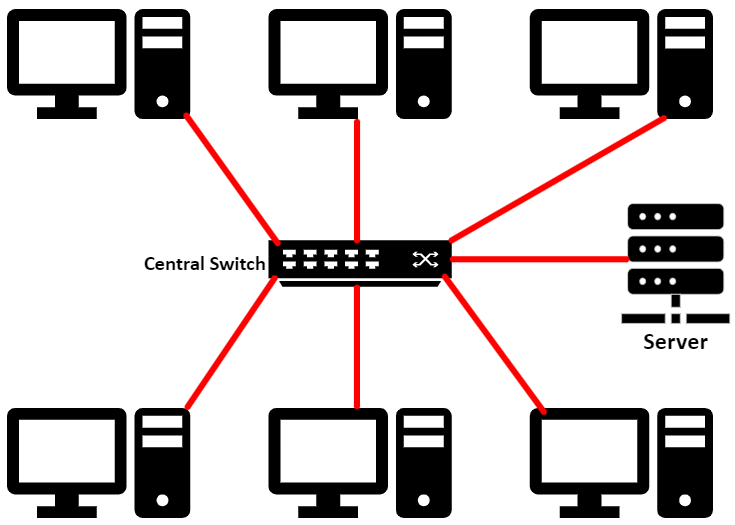
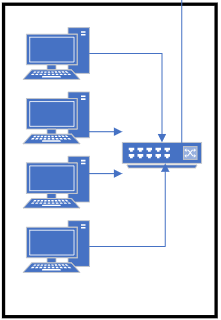
The star topology is named as such because when we draw a diagram it looks like…. a star – devices radiate out from a central point. Seriously.
Star networks have the following properties:
- A central node – nearly always a switch
- A single connection from the central node to each device
- Any number of connected devices (up to the capacity of the switch.)
Please take note that connections may be wired or wireless. Although diagrams always show lines (wires) for clarity, we can still create a star network entirely out of wireless devices.
Star networks are really common and are used all over the place in the real world. I am willing to bet that the computer room in your school is a star network – all the computers in that room will have a cable going into a central switch. There are clear advantages and disadvantages to this kind of network.
Advantages:
- Very easy to add new devices to the network – simply plug in a single cable
- Extremely easy to manage and configure
- Robust – if a device fails, which isn’t the central node, the network will continue to function
Disadvantages:
- If the central node (switch) fails, the whole network will stop working
- Can potentially be expensive in terms of long runs of cable or switch hardware
The central point of failure is the biggest problem with star networks and it is easily fixed by simply adding more switches to the network as redundancy – however, if we do this is then it is no longer a star network as there is no single central point! This takes us nicely on to the next type of network topology which fixes this reliance on central, single points of failure – the mesh.
Mesh
Mesh networks are slightly more complex than star networks and also often misunderstood at GCSE. We need to establish a few definitions before we look deeper into this type of topology.
A mesh network is any network where there are multiple paths to every or most of the destinations on the network. Meshes are very robust and solve the problem of relying on one single device in a network to route all traffic to its destination.
There are two types of mesh – partial and full.
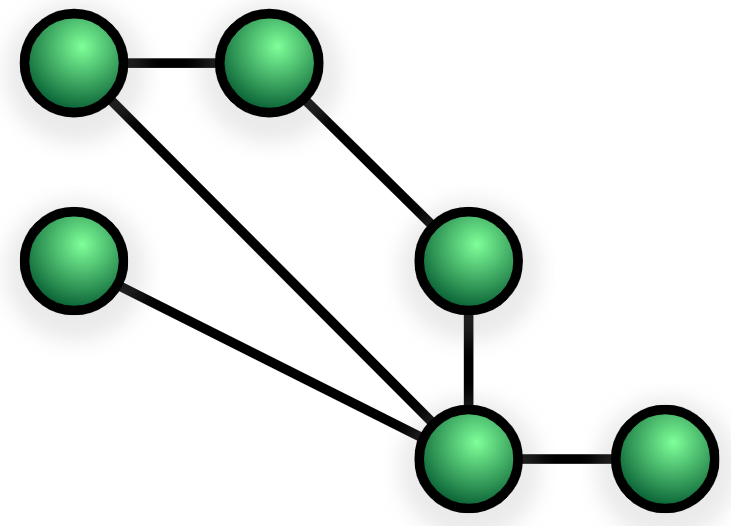
A partial mesh network is where most, but not all, devices have multiple paths or connections on the network. There is some, but not complete, redundancy.
This is effectively what the internet is. There are huge amounts of routers on the internet with multiple connections to other routers and networks which give redundancy. This is why, for example, if an undersea cable is cut the internet does not just grind to a halt – there are other paths to the same destination.
However, the internet is not a complete mesh, there are some nodes, some areas where there will only be one single route to a destination, usually on the edge of the network – to your house, for example.
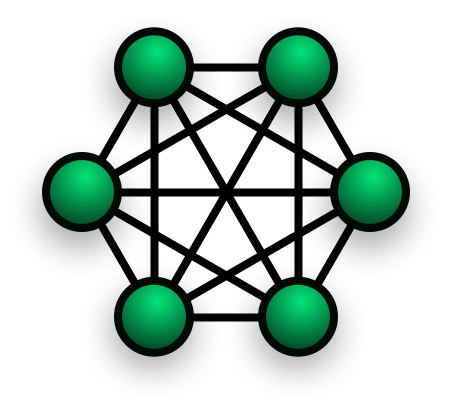
A full mesh network is one where all devices are connected to all other devices.
Core internet infrastructure routers will usually be connected in a full mesh structure to ensure maximum reliability, robustness and efficient data transfer between networks or nodes. Meshes such as this are expensive and complex to set up.
One thing that is often misunderstood is that the nodes on a mesh network, especially a full mesh, are not computers but routers or switches. Often, diagrams on the internet show meshes using computers as nodes and this is quite obviously madness. Whilst it is possible to create a mesh of computers, as you go past 3 or 4 devices, you would very quickly start to need computers that consist of nothing but network interface cards, which would be very silly indeed.
To summarise, mesh networks have the following advantages:
- Redundancy – there are multiple paths to the same destination.
- Redundancy – if a piece of hardware fails, even a switch or router, the network will continue to function
- Performance – Routers will be able to select a path based on the most efficient route
And the following disadvantages:
- They are more expensive to set up than other types of network due to the cost of cabling
- They are more complex than other forms of network
Network Hardware
To create a basic network you need very little in the way of hardware. However, if you want to do anything remotely useful or ensure robustness and high performance, then a variety of devices will be required. You are expected to know about a surprising amount of different network devices for your exam and so below each one is broken down into the essential information you’ll need.
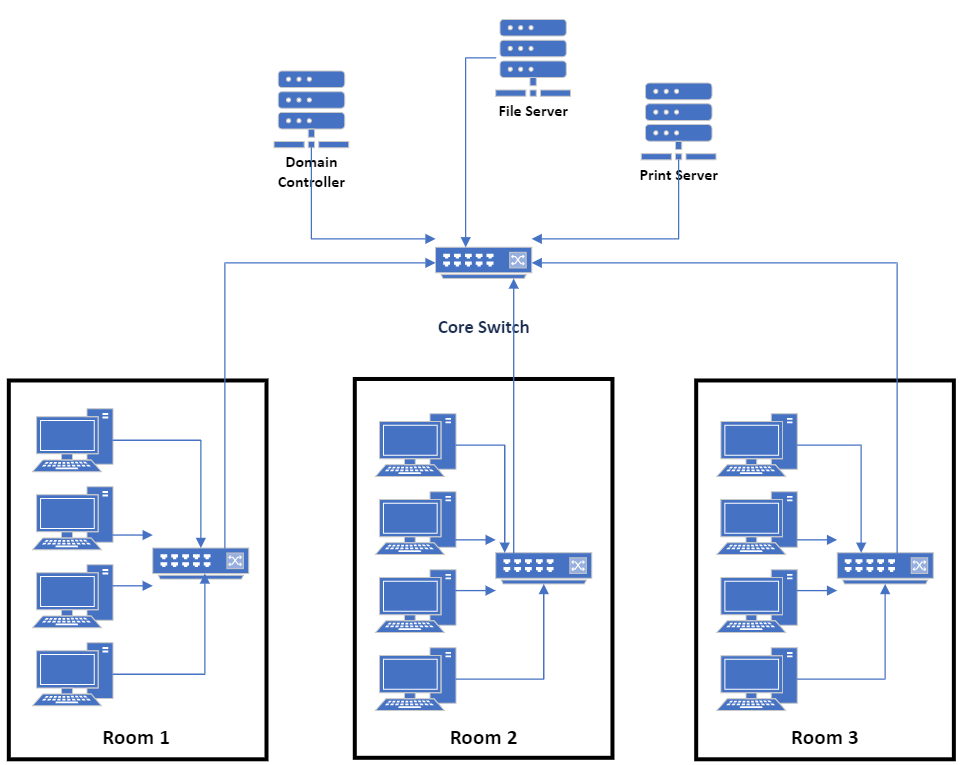
Switch

We’ve mentioned switches a lot throughout this page and that’s because they’re fundamental to how any network functions. Their sole purpose is to manage the traffic (packets) in a network to ensure that data is sent to the correct recipient.
A switch is:
- A central point on a network.
- A device which connects computers together in a LAN.
Switches are used on internal networks. If you think about a classroom of computers, each one will have a cable which goes somewhere… but where? The answer is to a switch somewhere in the building, usually in the same room or nearby at least. Those switches may be connected to other switches, and all of them will eventually be connected to either a server or to a router which allows access to the internet. So lets be clear, when we talk about switches, these are the devices which allow our computers to communicate on an internal network. Switches are LAN devices.
A switch will keep a record of the MAC addresses of each computer connected to it. MAC addresses are covered in detail in the next section – 1.3.2 – Wired and Wireless Networks, Protocols and Layers. For now, the following quick summary will suffice:
- MAC address = Media Access Control address, a unique identifier for a piece of hardware on a network. No two devices will ever share the same MAC, ever.
- IP address – each device on a network will be allocated an IP address. These are used by routers (and some switches – but this is beyond the scope of GCSE) on a network level to route traffic to the right place or the right network. IP addresses can change.
When a packet arrives at the switch, it will look at the packet to determine who it is for from the destination MAC address. If the destination device is connected to the switch, then it will deliver it to the intended recipient. This makes for efficient networking and doesn’t fill the network full of unnecessary traffic.
Switches are actually far more complex than we make out at GCSE, but fortunately we can generalise at this stage in our learning and simply summarise that a switch simply takes data from one port, checks the destination MAC and delivers it on the relevant port if that device is indeed attached to the switch.
A switch:
- Connects devices together on an internal network (LAN)
- Delivers packets only to their destination
- Uses MAC addresses to know whether a device is connected or not
- Does not generate excess traffic on the network – efficient.
- Switches can be quite large – up to 40 devices can connect to a single switch.
Disadvantages
- Switches are expensive to buy
- They will need some setting up initially on larger networks
- You may need to have an administrator employed who can look after them/set them up.
Please note: A switch is NOT used to connect a network to the internet. Please don’t mention the internet when talking about switches.
Router


Routers are massively misunderstood when people are learning about networks and unfortunately some of this confusion has come from large, well known companies using poor branding of networking hardware. In other words, they’ve used the wrong words to describe the devices you have in your house that connect you to the internet.
If you look at the pictures above, two popular home routers are actually sold and marketed as hubs. Clearly, these devices are not hubs at all – a hub (or repeater) is a device with no intelligence which simply broadcasts any traffic it receives to every connected device. Hubs literally flood the network with any traffic they are given and are a horrendous idea if you’d like to actually get anything done in terms of sending and receiving data.
If these devices are not “Hubs” then what are they? In the case of these home routers, such as the Virgin Super Hub and the Sky Q Hub or any other router provided by a broadband supplier, they are actually four devices in one:
- A Router (to connect you to the internet)
- A Modem (to convert signals from one form to another for transmission and receiving)
- A Wireless Access Point (to enable you to connect wirelessly to the device)
- A Switch (to enable multiple wired devices to be connected to your network)
So next time you hear a company advertising their latest “home hub” you’ll know it’s not a hub at all, so please don’t confuse these types of network devices. However, the most important part of any of these devices is the router part, so what is a router exactly?

A stand alone router has one core job – to connect networks together and route packets between them.
Now there’s quite a lot going on in that definition so lets break things down:
The internet is a network of networks and routers are the devices that sit between each of these networks and connect them together. This is just like a roundabout in the road network – lots of roads come together and we can pick a direction to continue on our journey. So, we can conclude our first characteristic of a router – routers are used to connect networks to the internet or to other networks.
Due to the fact the internet consists of thousands of networks all joined together, just like the roads we use every day, it means that there are many, many possible routes to any one destination. Think about it, if there are roadworks on your usual route to school, you don’t just turn round and go home because it’s impossible to get in, you can just take another way.
Remember, though, that there are no direct connections on the internet from source to destination. Data must travel through many intermediate points as it travels through each network on its way to and from the source and destination. This means that packets will travel through many routers on the way to their destination – the data must “hop” from one network to the next to get to its final destination. The next characteristic of routers we need to know then, is that routers forward packets on to other networks – closer to their destination.
To summarise:
- Due to the fact that the internet offers multiple routes to any one destination, the internet is robust – if one route breaks then another can be used. This behaviour robustness only works because of routers knowing where to send packets based on the state of the networks they are connected to.
- Routers can sense changes in the network like this and work round them – finding new routes to networks.
- Routers communicate with each other to notify other routers about changes to the network
- Routers can, and this is the really important bit, select the best path for a packet to take to reach its destination.
In your exam, you will need the following points:
- Routers connect LAN’s to WAN’s, or you can say routers connect LAN’s to the internet.
- Routers receive packets and forward them to another network, closer to their destination.
- Routers receive incoming packets and forward them to internal networks, to their final destination.
- Routers connect to other routers and communicate about available paths.
Routers, then, can be seen as “intelligent” networking devices, capable of talking to each other to coordinate the delivery of packets to their destination via the best path possible. Should a problem occur on the network, they will automatically find another path to the destination.
Network Interface Card (NIC) and Wireless NIC
One thing many people forget about when talking about networks and how they work, is that you actually need some specific hardware to actually connect to a network in the first place. This can be done using either a wired connection or wireless, but either way you will need either a:
- NIC – Network Interface Card
- WNIC – Wireless Network Interface Card

As you can see, these can come in many different form factors depending on the type of device being used. In most cases, devices such as laptops, tablets, phones and anything else that can connect to the internet will come with some form of network card built in – it’d be a bit weird if you had to screw a bit of circuit board to the side of your new phone to make it work on your home wifi, wouldn’t it?
The job of a NIC is:
- To enable a device to connect to a network using either a cable (wired) or radio waves (wireless)
- To turn data in to packets
- To receive packets and reassemble them in to data
- To manage the sending and receiving of packets
When asked the question in an exam “what hardware would be needed to create a network” or “what additional hardware does a device need in order to connect to a network” remember to mention some form of wired or wireless NIC!
Wireless Access Point

If you look hard enough in most buildings you’ll see one of these “alien space ship” designs in the ceiling or on a wall somewhere, blinking away. These are wireless access points, the things that “give you wifi” – which, by the way, is a completely inaccurate and wrong thing to say. Please stop mis-using the term Wifi. Why? Find out in the next unit which is all about how wireless transmission works!
Wireless Access Points are simply a node on the network which enable one or more devices to connect to a LAN without a cable.
The job of a WAP is:
- To allow a network to have wireless access
- To allow devices to connect wirelessly to the network
- To implement wireless security and encryption
- To allow devices to send data wirelessly
- To send data to wireless devices that they have requested.
Server
Servers are one of the most important devices that can be connected to any network. Before we get to the reason why, we must first define what a server is.
A server is any computer (usually very powerful with a large amount of resources), connected to a network, which has a dedicated role, purpose or authority over the network.
It is possible to create a server out of any computer, however most servers are specialised machines which usually have large amounts of CPU cores, huge amounts of RAM (many hundreds of GB) and a lot of storage which can be swapped in and out without turning the machine on. Servers are designed to be the most robust computers available that, once turned on, are never turned off again until they are no longer needed.
Servers get their name from what they do – provide a service. Servers are central devices in a network and they simply listen for requests made by clients (other devices that may need something). When a request is made, the server responds by sending out the relevant data.
You will need to know a few examples of servers and their function for your exam. You don’t need to know the really gritty details, an overview will suffice. Let’s look at some of the more common types of server and their roles.
Authentication servers
In a Windows based network, these are known as “domain controllers” and are the most important servers in the whole network. When you sit down at a computer in school, before you can use it you need to enter your user name and password to “log in” to the computer.
How does the computer know who you are, whether you typed in a correct user name and password and whether you are actually allowed to log on or not? Without a server, you would need every computer in the whole school to have a copy of the user name and password of every user in the school. This would be both silly and bad – the security issues alone are enough to have your average geek running for the hills screaming. So, how does this process work?
- When you type in your log in details, the computer sends a request to the authentication server (domain controller) to ask if you are allowed to access the computer.
- The authentication server is constantly listening for these requests.
- When it receives a log in request, it takes the user name and password details and checks them against its database of users.
- If you are not a user of the network, or you made a mistake in your log in details, it will send a response back to the client computer telling it not to let you in.
- If you are a user of the network and you got your log in details right, the server will sent a response back to the client computer telling it that you are allowed to log in.
- Finally, the server will send a list of rules to the client which will tell it what you can and cannot do on that computer. This is amazing for security.
Web Servers
Web servers are computers connected to the internet, with the purpose of holding web pages that are part of the World Wide Web (WWW).
When a user types in a website address into their browser, a request is sent to the web server for a copy of the web page the user wanted. The web server listens for these requests and sends back pages as and when they are requested.
Historically, this is all they did. However, in the modern WWW, they are responsible for so much more such as handling website log in details, processing online shopping, managing user data and any other dynamic/special features a website may provide.
File and backup servers
File servers, as you may imagine, contain a lot of storage. Their role on a network is really rather simple – allowing users to either request files that they have permission to see/use/modify or to store files on the server.
The huge advantage of using a file server is that user data is all stored in one central place in the network. It would be madness to allow users to store data on the machine sat on their desk – what if it breaks? What if they simply move desk or room? Their data would be lost.
By storing data on a server, a central point on the network, not only is their data available anywhere, on any device in the network (so no matter where they log in, they can access it) the network administrator can also easily back up their data to ensure it is safe. There is only a need to copy the data off the file server to a backup store and the administrator can be confident that everything is safe and secure in case of issues.
Summary
- Servers have dedicated roles such as logging in users (authentication), sending and receiving files (file server), monitoring network traffic and applying security rules (proxy/firewall) or sending and receiving email (mail server).
- Servers are used to control access to resources on a network. Only authenticated users may make requests to a server.
- Servers can secure a network – they will apply rules to client machines and administrators can apply security rules centrally (on a server) to any device connected to the network.
- Some servers may be public such as web servers and email servers. Some may be internal only, such as authentication and backup servers.
- As servers are such powerful machines, a single physical server may perform one single specific role, or be split up using software into “virtual machines” to perform many roles at the same time.