In the previous section, 1.4.1 – Threats to Computer Systems and Networks, we looked at a fairly comprehensive rundown of the most common and prevalent attacks that exist to compromise system security, steal data and gain access to computers.
This section focuses more on preventative measures – how can we ensure that computer systems are not vulnerable to the many attack vectors available? There are seven main methods of increasing security and decreasing the likelihood of becoming the victim of a cyber security breach. Whilst no computer system can be said to be completely secure, there are steps that can be taken to massively increase our defences to common and known attacks.
In this section (click to jump):
- Penetration Testing
- Anti-Malware
- Firewalls
- User Access Levels / User Access Rights
- Passwords
- Encryption
- Physical Security
Penetration Testing
Penetration testing must surely be one of the best jobs in the world. A penetration tester is someone who is paid or contracted to deliberately try to break through security – whether that’s physical security (security guards, members of staff in a business) or IT system security. At the end of an agreed period of time, they produce a report highlighting any weaknesses that need to be addressed.
What is it?
- A person or team of people are hired by a company. Very few people will know that the test is about to take place, this is to ensure the results are realistic as employees will not be expecting an attack.
- The penetration tester will then spend a period of time observing the company, its employees and its systems to gather information
- Once enough is known about the company, attempts will be made to gain access to the buildings and computer systems. This may involve:
- Impersonating employees
- Social engineering of staff
- Creating fake credentials
- Exploiting known security vulnerabilities in various systems
- Exploiting poor staff security – e.g. holding doors open into a building for people you don’t know, carrying data on removable devices, leaving computers logged in, leaving data out on desks etc.
- The penetration tester will attempt to steal as much as they possibly can during the agreed time
- Once the test is over, they produce a report highlighting all the security weaknesses they found.
How does it prevent attacks or help us recover from an attack?
- This is the best way to truly test the security of your systems and how effective security policies are
- It is one of the only ways to provide a “real world” test and see how employees of a company truly behave and how they are implementing security policy
- It will provide an in depth analysis of your current level of security
- It may highlight issues that had not been considered
- It will almost certainly improve security in an organisation
Anti-Malware
There used to be a golden rule in computing – the first thing you install after an operating system is some form of security or anti-virus software. These days we are more lax when it comes to security as operating systems have made huge leaps forward in terms of their inherent security but also, in the case of Windows, they now come with built in anti virus software which is automatically switched on. This is a huge improvement on the past, but is not a perfect catch all solution!
What is it?
The very opposite of Malware – software that is designed to detect, remove and prevent the installation of malicious software.
- Anti-Malware comes in many flavours – but you’ll usually know it as “anti-virus” software.
- These packages may have varied functionality but usually include:
- A file system scanner to find potentially malicious software
- Real time scanning of running programs to monitor for virus like activity
- Download/network connection scanners
- Some kind of utility that will attempt to clean a system / rid it of malware
- Because there are so many viruses and malicious programs, software like this will often use “heuristics”
- Heuristics is simply a “rule of thumb” approach to detection – if a program looks or behaves like malware then it will be flagged up/detected
How does it prevent attacks or help us recover from an attack?
- This is the most common form of protection a system may have. Malware detection is even standard in some operating systems now, for example “Windows Defender” in Windows 10.
- This type of software should protect systems from most, but not all attacks
- Anti-malware also helps to prevent the accidental installs of malware and should provide protection against “drive by” attacks when a user visits a compromised website
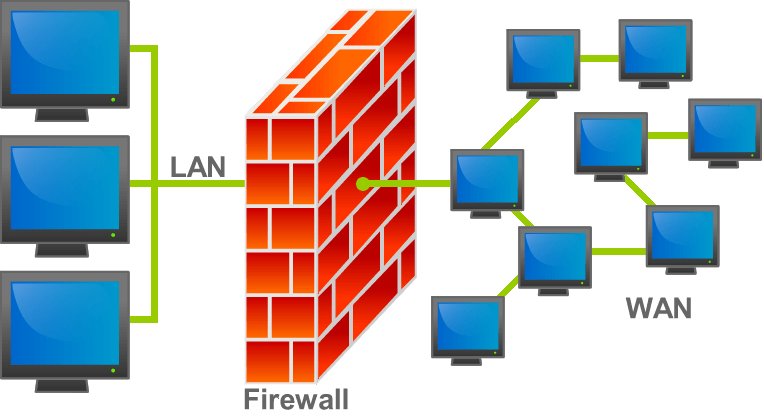
Firewalls

A firewall is a kind of gate keeper for your network connection. It examines all the packets that travel both in and out of a network connection and will allow packets to come in and out only if they conform to a set of rules that have been set. This is an absolute basic requirement of any kind of network security and often a first line of defence to filter out unwanted traffic. They can also be used to effectively “hide” sections of a network from the internet.
What is it?
- A firewall can either be software running on a machine or a physical piece of hardware connected to a network
- Firewalls will be configured with rules which are applied to both incoming and outgoing traffic
- Every packet that is sent through the firewall will be allowed or disallowed based on these rules
How does it prevent attacks or help us recover from an attack?
- Firewalls are one of the most effective methods of preventing malicious traffic from reaching a machine or network
- When properly configured, firewalls can prevent many vulnerabilities being exploited
- Firewalls do not stop people physically accessing a computer on the network, however!
User Access Levels / User Access Rights
Depending on your job or role in an organisation, you will require different access to computer systems. For example, an office worker will need to be able to use office programs, access the internet and have a personal area to store files and data. They would never need to be able to configure settings or install new software. An administrator, on the other hand, would require complete access to all aspects of the system in order to do their job.
What is it?
- Access RIGHTS:
- Set by administrators and usually implemented by policies when a user logs in
- Defines what a user can or cannot open or access
- Usually this relates to file shares
- Can the user read/write/modify/execute a file or program?
- Can also apply to programs
- Access LEVELS:
- Set by administrators and usually implemented by policies when a user logs in
- Defines what type of user an individual is:
- Admin
- Power user
- Standard user
- Restricted user/guest
- Used to apply different rules/types of access depending on what administrators have decided users should and should not be able to do.
- E.G. Administrators – all access to all systems
- Power User – ability to modify systems in a controlled way, perhaps install software or change passwords.
- Standard user – has access to the system, can perform tasks necessary to complete work but cannot modify system settings, install software or change data shares
- Restricted – has access to only a very small set of programs and data on the system. Think about your controlled accounts as an example, there is no internet access when logged in as a restricted user.
How does it prevent attacks or help us recover from an attack?
- Access rights and levels, if configured correctly, provide a robust way to secure access to computer systems – users should only be able to do what they need to and nothing more
- Access rights should stop users accessing data they do not have the right/need to
- Access levels and rights are only as effective if correct security procedures are followed – for example keeping passwords secure and never sharing log in information. If an attacker gains access to an administrator account then all security can be bypassed
Passwords
The future of security is biometrics and single use passwords/keys. However, for now, we are stuck with the concept of user names and passwords as a method of securing access to computer systems, websites, devices and so on.
Passwords should be unique and individual to each account they are used with. Furthermore, every password should be as randomised as possible, including a mixture of letters, cases, numbers and symbols.
You have learned in the previous section that computers are excellent at boring, repetitive tasks just like… guessing your passwords. A brute force attack can prove surprisingly effective against many passwords, especially those of a short length. Worse still is a brute force attack using a dictionary – the internet is full of “known” passwords and these lists contain millions of passwords that have been stolen during security breaches. If you use one of these, or one similar, then the security of your account can be measured in milliseconds.
Let’s presume, to make your password memorable, you use your dogs name. How secure is that?
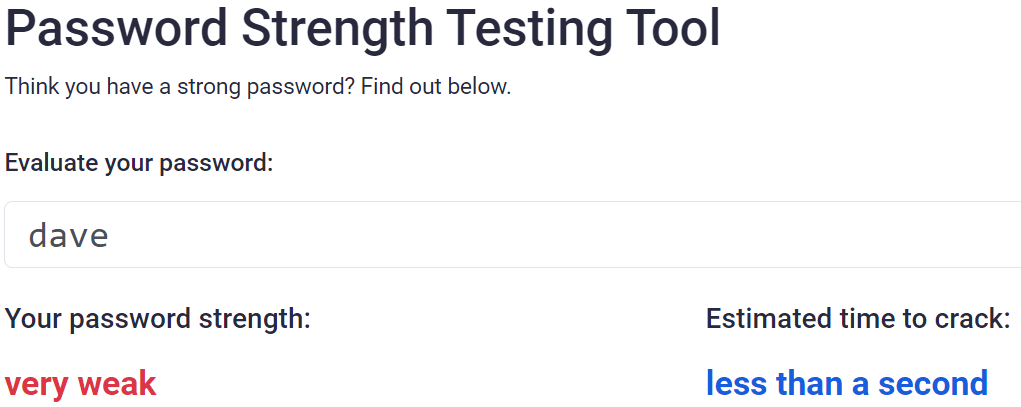
Oh.
Can we do better? Well, we know that longer passwords are more secure. What about davethedog?

Oh…
Ok, well we bought Dave the dog in May 2020, so let’s add that as numbers to the end:
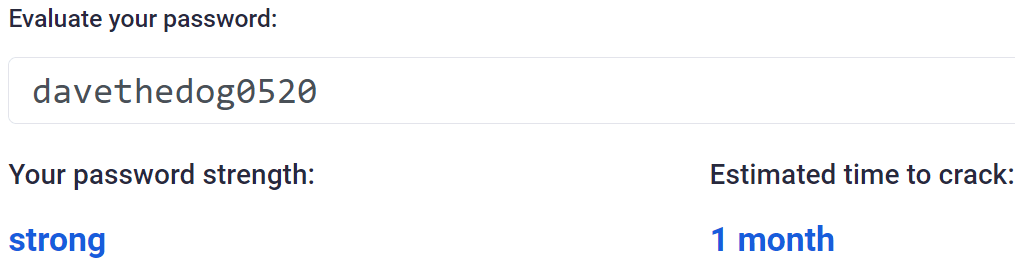
Now we’re getting somewhere, but it still isn’t great. Can we improve further? Let’s try adding some case changes:
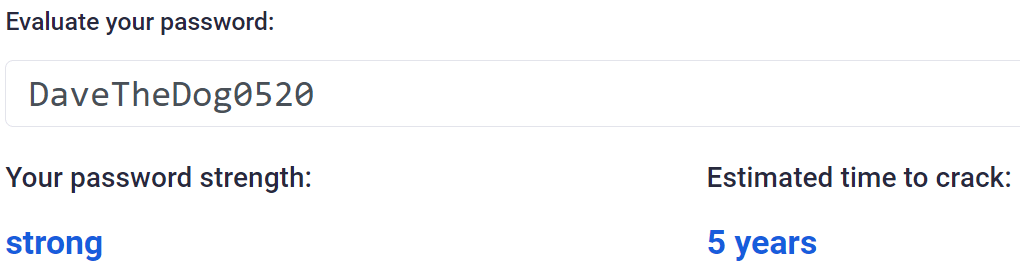
Now we’re talking. For the sake of three capital letters we’ve added a few years of security to our account. Theoretically! If someone knows your dog is called Dave then you’re back where you started. Can we go further? What about numbers where letters normally would be?
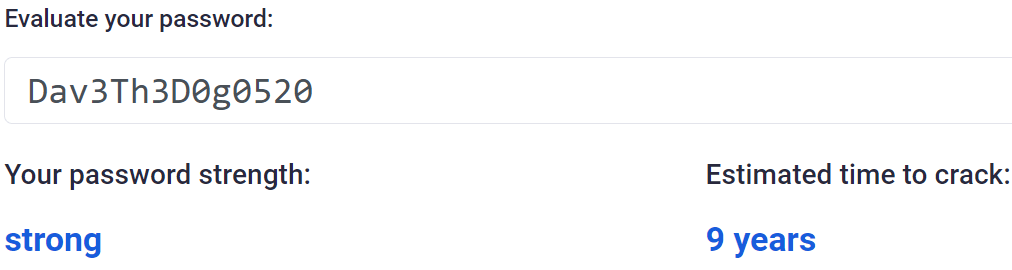
Better, but not quite the giant leap we’d expected. There is one more thing in our password armoury though and that’s symbols. Let’s say we really want to emphasise how much we love Dave:

Wow! An extra 82 years and just for the sake of a symbol.
The only downside here is that the more secure we make our password, the harder it is to remember and the slower we will be typing it in, giving someone looking over our shoulder the perfect opportunity to just write it down.
There are two answers to this. First, just use a password manager. These will take care of generating long, random passwords for you that are unique to every account. You will never need to remember a password again and they can be copy and pasted in when you need them. Here’s an example for a randomly generated password which is exactly the same length as our Dave the dog effort above:
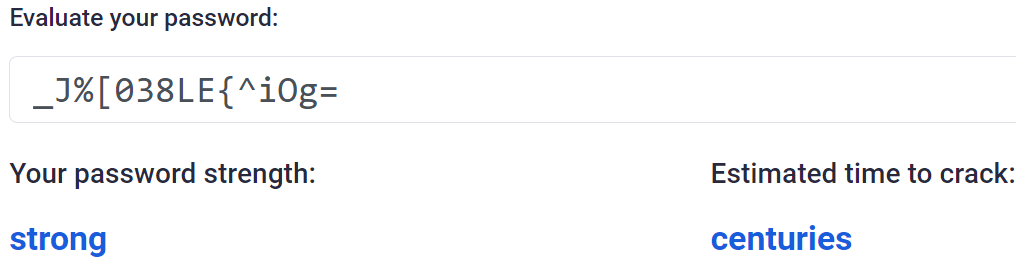
Much better, plus there is no way on earth that’s going to appear in any password lists unless the system is compromised – in which case, you’d have changed your password anyway and because you’re using a password manager that compromised password won’t affect any of your other accounts because they’re all different.
The second option, if for some reason you won’t use a password manager, is to use stupidly long story based passwords.
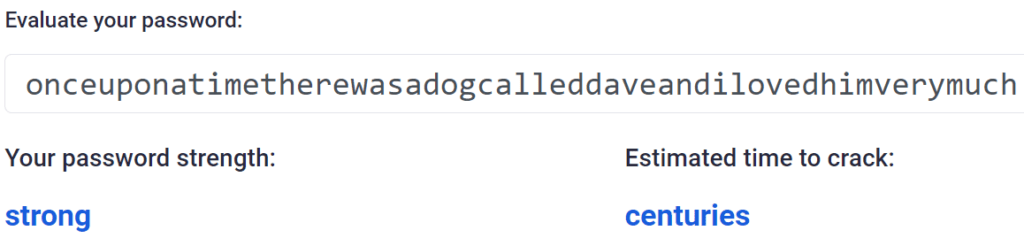
Again, however, you’ve got the remembering problem along with the temptation to re-use your password everywhere. Just get a password manager.
To summarise, for your exam you need to know:
- A password is a string of characters
- It is used to uniquely identify you in conjunction with a user name
- Password strength is affected by length, case, randomness, use of symbols, use of numbers
- Common words or phrases are easy to compromise and are a security risk
- Passwords need to be unique between accounts so that if one is compromised, the others are not at risk.
If you want to test the strength of your passwords, you can do so here: https://bitwarden.com/password-strength/
You can make use of password generation and storage on most modern Apple or Google phones. Just be careful, however, as your passwords are stored using proprietary apps like Keychain in the case of Apple and this limits you when you want to access your passwords on another device such as a Windows PC or a smart TV for your Netflix account or similar. It is often better to use a dedicated, centralised password manager.
If you’d like to use a password manager, there are multiple options available and you do not need to pay someone for a password management service. If you want to synchronise your database of passwords between all your devices, simply save it to OneDrive, Google Drive or iCloud Drive. The database is encrypted so you should be safe in the event of it being lost or stolen.
A good place to start might be : https://keepass.info/ for Windows based devices. Mac users can download the alternative app AuthPass and IOS users can use KeePass Touch. All are compatible with each other and the same database can be used between all of those apps.
Encryption
Without encryption there would be no internet as we know it today. All of the good things we can do such as order a meal without moving off the sofa, buy a car at the tap of a button on an app or write a job application without someone stealing our personal data can happen because we have access to strong encryption.
Encryption is the scrambling or encoding of data so that it cannot be read or understood if it is intercepted or stolen.
Encryption has been around for centuries in the form of codes and ciphers that people have used to keep things a secret, to stop other people from understanding communications. The most famous of these are probably the Enigma and later Lorentz ciphers used by the Germans in World War 2.
The problem with all ciphers, including Enigma and Lorentz, is that if you take the steps used to encode the message, you can reverse these steps to decode the message. No matter how complex and convoluted you make the encoding method – if you know the method then there is no security as you can simply reverse the process to decode the messages.
This created what was known in mathematics circles as “a problem.”
To create truly secure communication you need to have a method of encryption where there is one method to encode the message and a totally different method to decode the message.
If we can do this, then it doesn’t matter if someone knows how you encoded your massage, reversing the process will not work! This kind of mathematical magic was thought to be completely impossible until the 1970’s.
Shared Key Encryption (or Public/Private Key Encryption)
Modern encryption uses something called Public/Private key encryption. It works like this:
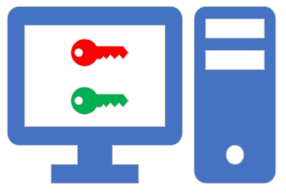
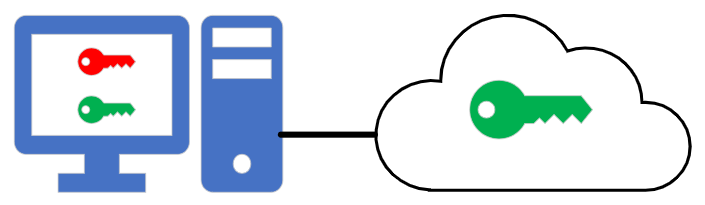
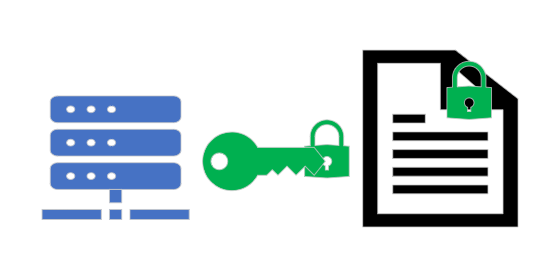
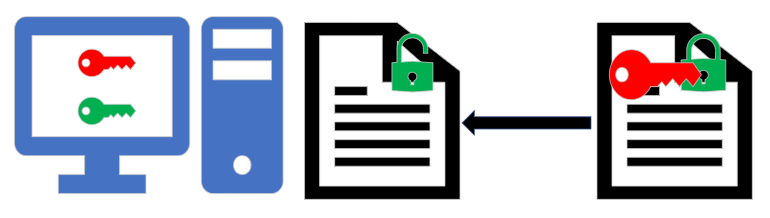
The only way in which this method of security can be realistically compromised is if the private key is stolen or lost.
This is a huge simplification of how public / private key security works, but it is enough for your exam! Here’s that summary again:
- A user who wishes to establish a secure connection with another device uses an algorithm to generate a public and private key pair. These keys are different.
- The user makes their public key publicly available!
- The remote device takes this public key and uses it to encrypt the data that it sends back to the user. Anyone can intercept this data, but the public key will not decrypt it.
- The user receives data that has been encrypted using their public key and decrypts it using the private key.
Physical Security
Every method of security we have looked at so far has concentrated on protecting computers that are in some way connected to a network or the internet. Being connected to a network is itself a security risk – if you can reach a device then you can attempt to compromise that device.
If ultimate security is the objective then there is no better method of ensuring a device cannot be accessed than physically disconnecting it from any kind of network connection.
Physical security means:
- Not having a network connection at all, or being on a completely physically separate and isolated network to all other devices
- Being in a room or space where access is controlled, for example by lock and key, security staff, code access or similar
- Not allowing any external devices such as hard drives, memory cards and USB memory sticks to be connected to the computer
- Having complete control over who can and cannot physically touch and use the machine
With physical security there are only really two remaining threats to the security of data contained on that particular device:
- The person allowed to operate the device has access to material and they could quite possibly sell that information to others. You cannot control the contents of their brains!
- Connecting any form of external device in order to steal data. This, however, should be blocked using policy/access restrictions in such a scenario.
There is no such thing as 100% guaranteed security. The only true guarantee of security is the physical destruction of a machine and then… it isn’t much use any more. There are always attack vectors that could be exploited to gain access to a machine such as social engineering or trojans stored on storage devices, for example. Keep this in mind when discussing security in your exam!