As the number of network connected devices increases, so does the proportion of poorly designed and insecure devices. Many people do not understand the significance of poor security, whether that is in devices they own or their own personal security such as selecting weak passwords that are easy to guess or compromise.
Any device which is capable of connecting to the internet or an internal network could be a potential point of entry for someone who wants to steal data, observe what is happening or use your computing resources as part of a network of compromised devices (a botnet) which can be used to attack other systems without your knowledge.
Security is no longer the responsibility of experts or network managers, it is something which should concern everyone. More and more of our personal information is stored electronically, online or in personal devices and this data is incredibly valuable in the wrong hands. This section is all about the most common forms of attacks that are used to compromise either physical or personal security. For your exam, you need to know what each type of attack is, how it works and how you might protect yourself against such attacks.
In this section (click to jump)
- Why is security important?
- Malware
- Phishing
- Social Engineering
- Brute Force Attack
- Denial of Service
- Interception and Theft
- SQL Injection
Why is security important?

Why is hacking such a big deal? It really isn’t as simple as in movies and certainly nothing like that famous episode of CSI where one character offers to “create a gooey interface using Visual Basic and see if I can track an IP address.“
Breaking in to computer systems is usually surprisingly difficult. Hours of painstaking research goes in to finding vulnerabilities, writing code and tools to effectively exploit weaknesses in software and hardware and the constant battle between those bad actors and the security and operating system companies that work to thwart their efforts. Why, then, do people do it? And why do people worry about it?
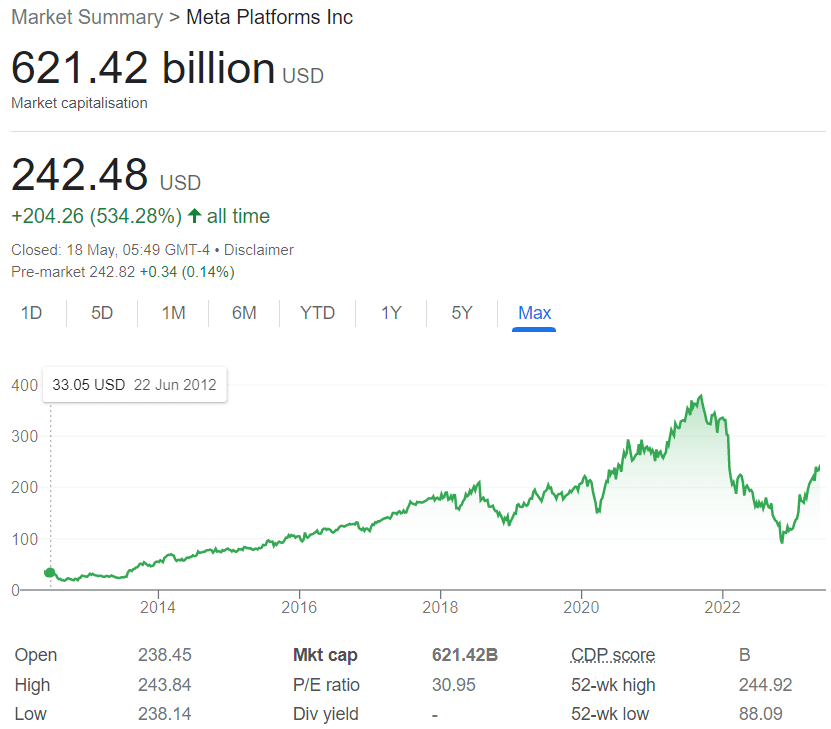
The answer to these questions is simple – it is all about data. Data is worth a fortune. In fact, it’s worth so much that the value of practically any big business today is largely based on the amount of user information and data it has collected. Sounds mad, wrong even? Well, think about it… Facebook floated on the stock market in the US for an initial offering of $38 per share, and its value peaked at $108 billion dollars on the first day of trading.
At the time of writing, Facebook is currently worth $621.42 Billion. More than half a trillion dollars!!! Yet it’s totally free to use?! Something doesn’t add up. How can a free service be worth so much money? How is that information in any way useful?
Stop and think for a minute – what is Facebook? On the surface, nothing more than a collection of what people had for dinner, people having very public breakdowns in their relationships, people selling tat to each other and posts from click bait farmers of “motivational” pictures or “you won’t believe what they did next!!!!!” links. *sigh*.
That’s worthless, right? Wrong.
Sadly, for the users of any social network, you are giving away some of the most valuable data ever collected in human history. I’m not exaggerating. Before the rise of social media, never had organisations been able to know so much about you and trust me, they tried. Companies 15 or so years ago would’ve ripped your hands clean off if you’d told them you could target exactly the people who are interested in your business – and now, because you give your information away for free, they can!
Your data, even the data you didn’t know you had or are passively giving away, is worth so much that investors are willing to pour billions of dollars in to the companies that hold it and…. you give it away for free!
If you have a smartphone, in one way or another, in one app or another, you have probably agreed that the following data can be collected, analysed and used in any way a company cares to use it:
- Usage data (this is massive) such as:
- How often you use your phone
- Which apps do you use?
- When do you use them – what time of day?
- How long for?
- Where do you use them?
- What do you click on?
- What do you share?
- How long do you look at a page/post for?
- What comments do you make?
- Location and movement data:
- Where do you live
- Where do you work (you don’t need to tell it, the phone can work this out easily for itself)
- Where you frequently visit
- How long you spend in certain places
- If you pay for things – how much and where?
- How you travel
- How active you are – even to the point where it could work out what kind of lifestyle you have.
- Your personal habits, preferences, likes and dislikes
- Everything you do on social media (and many websites) is tracked. What do you look at, how long for, what do you click on, what do you like? The list is endless and it builds a very accurate picture of you as a person which can be used in many ways by advertisers and businesses.
This list could go on and on, but I’d hope it gives you just the slightest insight into the wealth of data technology enables companies to collect, store and investigate. Some of this data collection is good – Google for example have done projects where they’ve tracked the evolution of the English language over time. Other data collection is solely for making profit at your expense. It’s getting to the stage where we’re verging on creepy behaviour by social networks, for example, Facebook in 2017 said they know enough about their users to be able to tell what mood they’re and in and what state of mind they are likely to be in! *shudder*
Still not enough? Well, what about if I said that Facebook know when someone rings your doorbell?
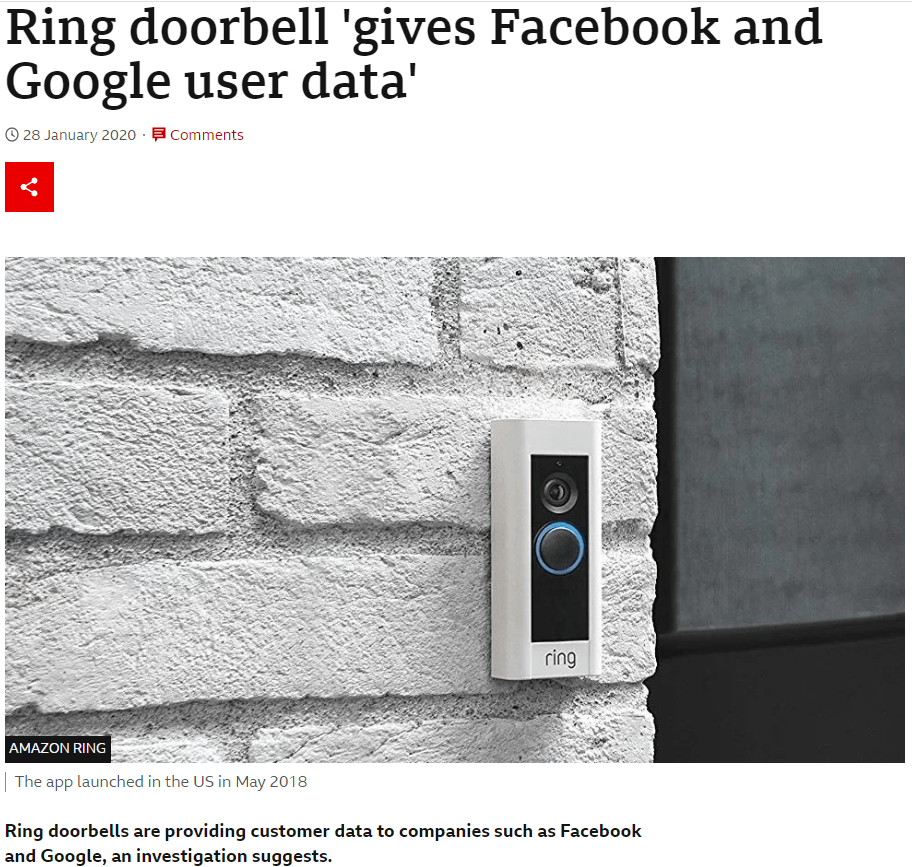
You are living in a time of utterly frenzied data collection. Companies are desperate to sell, buy and share your data in order to know more about you and ultimately sell more products. Your privacy is merely collateral damage. So much data is collected that companies literally do not know what to do with it. It even has a name – “Big Data” and it is the “next big thing.”
I’d hope that we’ve clearly established that your personal information is worth an absolute fortune and sadly, we all give it away for free in return for the ability to share and view mindless pictures with text on, videos with large text above and below telling us what the video is about (because clearly we can’t work it out for ourselves) and endless crying laughing face emojis next to things that are not funny in the slightest.
This is just the legitimate side of data collection, the stuff we agree to. What about the really personal data that a criminal might want to steal from us – such as our very identity?

We’ve changed the way we communicate in recent years, making it harder and more frustrating for law and security agencies to invade our privacy and listen in to what we say. However, please don’t ever think your communications are secure, they’re not. The NSA has a really interesting toolkit for intercepting anything you do and controlling your smartphone in any way they like.
This means that now, more than ever, more and more people want access to our data and they’re prepared to steal it from you to make profit. Criminal gangs actively try to steal entire customer databases from businesses with the intention of selling your identity, bank and payment details online for a small fee. You need to care about your privacy and security.
Attacks on computer systems or databases take three main forms:
- Physical – Either taking data on a physical device such as memory stick or laptop, or physically accessing a system and taking data.
- Remote – Accessing a system through a network or the internet in order to compromise security and take data.
- Socially Engineered – Tricking an individual or organisation into simply giving away their data.
There are multiple methods of carrying out each kind of attack and more are being developed every day. We need to look in to the most common methods.
Malware
What is it?
Malware is:
Any malicious software designed to damage data, spy on user actions, cause a system to malfunction or behave in an unwanted way.
Users usually fall victim to malware by:
- Clicking on links in emails which then download the software onto a device
- Opening attachments which contain malicious code
- Visiting websites which have been compromised so they automatically install or run malicious code on user devices. Sometimes this is called a “drive by” attack and is exactly how the NHS computer systems ended up with ransomware on them in 2017.
Examples of malware include:
- Viruses
- Key Loggers
- Root Kits
- Trojans
- Ransomware
- Spyware
Lets look at each in turn.
Viruses
What is it?
A virus is software that is designed to replicate itself – this means it will try to automatically copy itself to as many devices as it possibly can (just like, er… a virus?)
How does it work?
- Viruses are spread usually via email as attachments, but can also be spread via USB memory sticks, memory cards or any other removable storage
- Once activated the virus will immediately try to spread itself. This may be by sending itself to all contacts in an email program or copying itself immediately when a computer is connected to a memory stick or drive.
What does it do?
- Viruses are usually designed to take advantage of weaknesses in the security of a program or system
- As a result they may:
- Deliberately damage or delete data on a system
- Stop programs from working or delete certain programs
- Slow down a computer
- Make the computer vulnerable to further attacks.
How can you protect yourself?
- Don’t open email attachments or emails from people you don’t know!
- Don’t visit “suspect” websites
- Don’t plug in USB Storage or devices without some form of anti virus software on your system
- Have up to data anti virus software
Keyloggers
What is it?
A keylogger can be either hardware or software. It is designed to record every key that is pressed on a keyboard, therefore giving access to all the data that is entered into a computer such as usernames, passwords or websites visited.
How does it work?
- A hardware key logger would be plugged in between your keyboard and computer. They should be obvious, right? But let’s face it, when was the last time you looked at the back of your machine? Ah, many an hour has been whiled away looking at the various sockets on the back of a PC…
- A software keylogger will be silently installed on your machine and will simply save all key presses to a file.
What does it do?
- At regular intervals the key logger will try and send the data file to another computer or a server on a network where the data can quickly be analysed to remove passwords, websites and user names.
- Remember that a keylogger will also record the content of any messages or emails sent or any work carried out, meaning this is incredibly bad if you are working on sensitive or important information for a company.
How can you protect yourself?
- Don’t use public computers!! This is the most common target for hardware key loggers. If you have to use a public PC, check the cables and what they’re plugged into!
- Never use public wifi
- Check the back of your own PC if you’re paranoid
- Use up to date anti virus or anti malware software (although these don’t guarantee to catch key loggers)
- Follow all the rules for not getting a virus
- If in doubt, format your PC and start again.
Trojans
What is it?
A trojan is a program which is designed to deliberately trick a user in to downloading and installing malicious software. Trojans often look like innocent programs such as system utilities or even forms that need filling in. Trojans “hide” things like viruses or ransomware which are wrapped up inside a legitimate looking program.
How does it work?
- Users are tricked into downloading a file or program which looks innocent. A trojan can be disguised as any type of program, which makes them difficult to spot, however signs to look out for are:
- Programs or files sent via emails
- Programs that are “free”
- Programs from websites that you’ve never heard of, or just “feel” wrong.
- Sometimes, if a website is compromised, program downloads that are genuine and legitimate may be altered to hide malicious software.
- Upon opening or running the program, malicious software is silently installed on the users computer without them knowing.
What does it do?
- The effect of a trojan horse can vary depending on its pay load. Trojan horses usually hide code which is:
- A virus
- A “backdoor” which leaves your computer open to remote control, use in “bot nets” or data theft
- Ransomware
How can you protect yourself?
- In exactly the same way as you’d try to prevent viruses.
- Never, ever download software from an unknown source – if it looks too good to be true then it probably is. Also avoid “flashy” websites that try too hard.
- Sometimes trojans mimic Windows themes, so some older ones will look like part of Windows XP or 7 – this is usually a sign something smells of rodent.
Ransomware
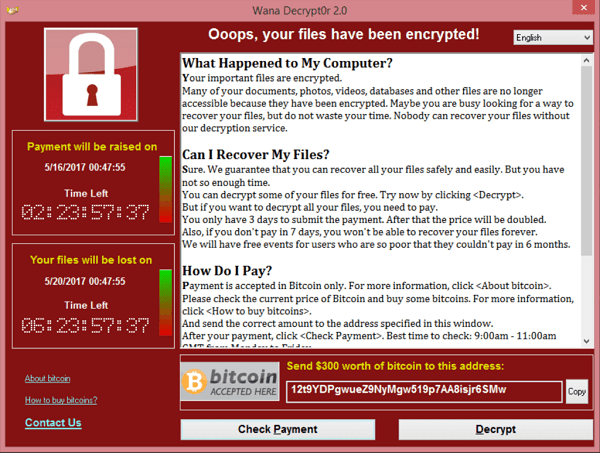
What is it?
Ransomware is one of the more modern types of malicious software and often very effective. It encrypts files and then demands a payment from the user to “unlock” them.
How does it work?
- A user visits a website which has been compromised. They become the victim of a “drive by” attack where code on the website automatically downloads and installs the software or…
- As with many forms of malware or virus, a user clicks on a link in an email which downloads the ransomware, or the ransomware is delivered as an attachment.
- When the ransomware is opened, it almost instantly begins to encrypt files, spread itself to other machines like a virus and demands payment from the user.
What does it do?
- Ransomware uses very strong encryption to scramble files on the target computer. Ransomware usually targets documents, images and sound files.
- A message is then displayed to the user which demands payment to unlock the files. Payment is usually demanded in BitCoin or other crypto-currency to make it difficult to trace.
- There is almost a 100% certainty that any user that does make a payment will not recover their files.
How can you protect yourself?
- It can be very difficult to protect yourself against ransomware if you are the victim of a drive by attack on an infected website, or if it is delivered by a trojan,
- As always, up to date security software is essential
- Don’t open those attachments!
- Finally – take a back up of your files regularly!! This is the only way you can sensibly recover from ransomware.
Root Kits
What is it?
Rootkits are malware which is loaded before the operating system and therefore gives complete control over a system, usually bypasses all security on a system and is undetectable by the operating system. Rootkits are a particularly nasty form of malware as once installed even anti virus software will have a hard time finding it.
How does it work?
- A Root kit works by installing itself in either the BIOS/UEFI or very early on in the boot loader of an operating system.
- This means it is undetectable by the operating system as it loads before any part of the OS that would realise has loaded.
- Consequently this means a root kit can bypass ALL security measures on a computer without detection
What does it do?
- Rootkits are often used to gain complete, admin/super user access to a computer, enabling someone to do literally anything they want with the target machine.
- This might include covert surveillance of a user and the collection of their data
- Adding the machine to a “bot net”
How can you protect yourself?
- Root kits are really, really hard to protect yourself against because of how they work. You can have the latest, up to date security software and still not know your machine is infected
- Sony once installed root kits on peoples machines! That’s nice of them…
- As usual – good security practise goes a long way. Do I even need to repeat the list of things you should and shouldn’t do?
Spyware
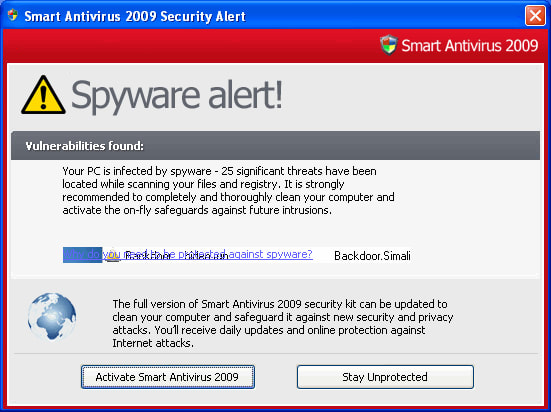
What is it?
Spyware comes in many forms, sometimes as a stand alone program and sometimes is a feature of other programs. It has one purpose and that is to collect data about the user/machine it is installed on.
How does it work?
- Spyware is usually installed in an almost trojan like manner. Software may be presented as a system utility, a free tool or similar which might “improve your pc performance!”
- Sometimes spyware is simply part of another piece of software. It has been argued that Windows 10 is spyware because even on “reduced” settings, Microsoft collect data about how you use your machine and send it to their servers so they can analyse how people use Windows.
What does it do?
- Once installed, spyware will start collecting information about the machine and users. Usually this data is web browsing habits and “program metrics” which is a posh way of saying “how do people use the software and what do they do with it?”
- More malicious spyware may well try to collect email addresses and other personal data which can be used to either send unwanted advertisements or as part of wider ID theft.
How can you protect yourself?
- Do not download and install software unless you know what it is/does and where it is coming from.
- Use reputable programs from reputable sources
- Don’t download “anti-spyware” software as, ironically, most of this is spyware itself!
Phishing
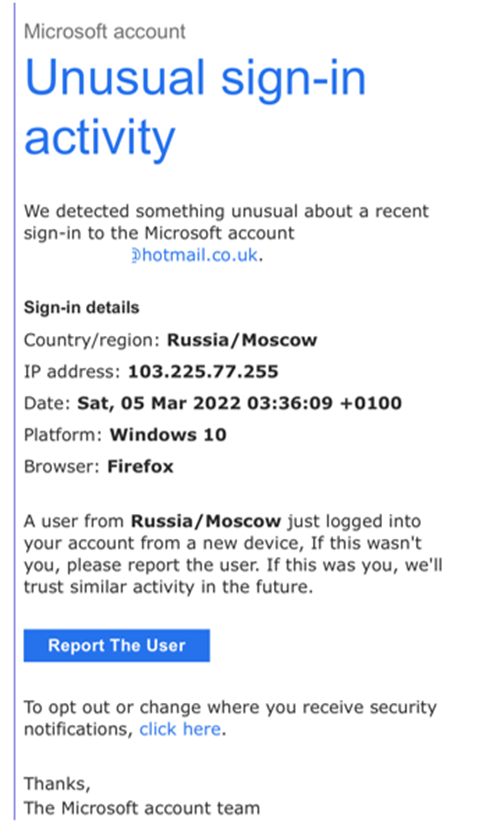
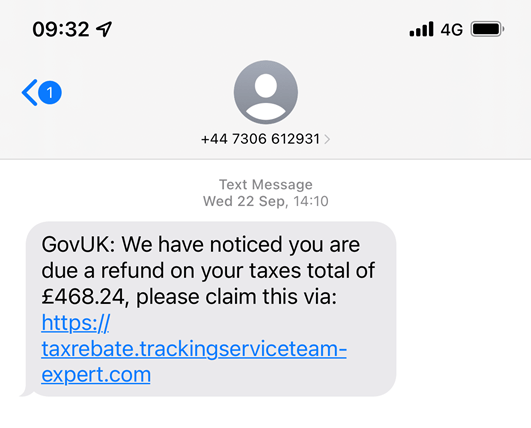
What is it?
Phishing scams are designed to make the job of getting your usernames, passwords and personal details as easy as possible. Instead of going through the difficult process of finding security weaknesses or trying to crack a password, for example, a malicious actor simply… asks you for your information.
Phishing is a form of social engineering. An email or text message is sent to the victim, which looks at first glance to be from a legitimate source/company and fairly plausible. The key to this attack is that users are encouraged or persuaded through fear to click on a link in the email or text. This link takes the victim to a copy of a real website where users will enter their user names, passwords and so forth which are then compromised by the attacker.
Usually, phishing attacks are quicky acted on by the attacker. They are alerted that someone has entered details and then they move to log in to accounts, place orders or transfer money before the victim realises something is wrong.
How does it work?
- The victim is sent an email or text which looks like it has come from a bank, government source or other well known company
- The email contains information designed to scare, shock or hook a user with an offer (usually “you are owed money”)
- The email then has a link for users to click on to “take action”
- Upon clicking the link, users are taken to a fake website which will collect any data entered
What does it do?
- Phishing scams are a form of social engineering and they are used to gather really valuable data such as bank details
- Phishing is incredibly easy and profitable for criminals because there is no cost or effort in sending emails
- There is also no “hacking” involved as users are, sadly, just giving their details away to criminals
- Once collected, the data is either used for fraud, theft or offered for sale for others to use on the “dark web”
How can you protect yourself?
- Does it sound too good to be true?! Then it is!
- Don’t. Ever. Click. Links. In. Emails. (or text messages)
- If you’re still in any doubt – call the company concerned. Tell them about the email and ask their advice. Make sure you get the number from their website and not from any dodgy emails you’ve been sent!
Social Engineering
What is it?
Social Engineering is simply the use and abuse of trust to gain access to passwords, sensitive information or computer systems.
As you know, Phishing is one form of social engineering. Social Engineering itself is based on the premise of “people are the weakest point in any security system.” This is largely because people want to trust, we trust those seen as being in positions of authority, we want to believe in other people and that they are doing the right thing. Socially, we find it very difficult to call people out and ask difficult questions – it is much easier to just accept a situation and go along with it than to challenge any doubts you may have.
Social engineering comes in many, many forms but it can be as simple as just asking “could you log me in to this machine, I’m having trouble with my account and want to check it’s not just me.” What would you say in that situation…?
Sometimes it will involve more elaborate set ups, such as dressing up as a person of authority, or in work clothing that makes an attacker look like they fit in to an environment. They may use observation and other data gathering methods to understand how a company works before confidently just walking right through the front door, stealing data and even physical equipment.
How does it work?
- Criminals usually pose as employees from known organisations and gain the trust of the victim by:
- Using shock tactics – “We’re the police doing an investigation and your bank account has been compromised” or “Hi, I’m from Microsoft and during a routine scan we’ve realised your laptop is infected with a virus, we’d like to help.”
- Using language you’d expect of an employee or someone who “knows what they’re doing.”
- If in person, simply looking the part – wearing official looking ID, dressing in company attire and mixing with real employees
- Once the criminal has gained trust or access they simply abuse the good will/trust of the victim and either trick them into giving details or simply asking for the information they want.
What does it do?
- Sadly, social engineering is one of the most effective methods of “hacking” that there is, and humans are nearly always the weakest link in any security system.
- Think about it – if someone posed as a manager, high up in a company that you worked for; or even as IT support for your company and started asking you to do things or give them your log in details so they could “diagnose a fault” then… you’d give them the information, wouldn’t you? After all, not many people are prepared to argue with their manager!
- Social engineering relies on gaining trust and looking the part. Unfortunately we are all built to be nice, trusting, honest people and sadly that’s easy to take advantage of.
How can you protect yourself?
- If you receive a call from anyone asking you for any personal information, security details or “just some information to pass through security” or anything that even seems slightly out of the ordinary – end the call.
- Any company that has your details and needs you for anything serious will be able to write you a letter – tell them to write to you or, in the case of a bank, send it to your local branch
- Call the organisation yourself and ask them if they have been trying to contact you.
- Do not believe anyone who tells you your computer needs attention, to download software so they can fix it for you
- In a work place, if you are unsure of a request, simply respond “I’ll be happy to help you out, I just need to check the details with my supervisor/manager first.” or “I’ll call you back when I’ve had time to process that.” Then do just that – check with someone that it is normal for another department to call up and ask for information.
Brute Force Attack

What is it?
Brute Force is the most crude method of trying to gain access to a system. It is quite simply trying every single combination of possible username/password until a system lets you in. It is often used as a last resort when other methods to compromise security have failed, or when the attacker suspects short or weak passwords have been used – in this case brute force attacks can be devastatingly quick and effective.
Definition: The constant/systematic use of trial and error (or a dictionary) in an effort to discover login information and gain access to a system.
To put that in context, it’s like if you came up against a code lock with 4 digits, you know there are only 10,000 possible combinations and it has to be one of them, so you start at 0000 and just keep clicking up towards 9999 one by one until it unlocks!
Clearly the problem here is complexity. The more complex the password, the harder it is to break. Complexity is increased by:
- Length – how many characters is the password?
- Using a mixture of letters, numbers and symbols
Passwords these days should be at least 10 characters in length to ensure they are robust enough to not be vulnerable to brute force attacks. Click here to learn more…
There is one way to improve brute force and that’s to use what’s called a “dictionary attack.” A dictionary attack is where:
- A huge list of (potentially hundreds of thousands or even millions) of known passwords are stored in a file
- These are usually gathered from hacks and compromised websites – so they’re real passwords people have used
- The program then tries each password from the dictionary to see if it works
- This is much quicker and usually successful due to people using easy/memorable/common passwords
Denial of Service
What is it?
Denial of Service or “DDOS” – Distributed Denial of Service is not necessarily a method of breaching security or “hacking” a system. It is the act of using a constant stream of requests sent to a server to make a website unavailable and to appear as if it is no longer online.
How does it work?
- Usually a denial of service attack is carried out using a “bot net.” A bot net is simply a huge list of computers that have been compromised by trojans, back door software or other security breach. Computers in a bot net can be remotely controlled and their internet connections used to send data anywhere a criminal decides.
- Hackers/criminals will often sell access to a bot net, often selling access to blocks of hundreds/thousands of machines
- The bot net is then used to send a flood of requests for data to a single web server
What does it do?
- Once the flood of data requests is sent, the server receiving these requests begins trying to address these requests
- Eventually, however, the volume of requests becomes higher than the server is able to handle and so it begins to time out/not respond to requests
- Any legitimate requests made during this time are effectively “lost” as they too time out and the website appears to be offline.
How can you protect yourself?
- Hope that the men/women with beards in your organisation know what they’re doing and can mitigate the effects of a DOS attack.
- Install all security updates, patches and software updates on all networking and network connected hardware.
Interception and Theft

What is it?
Sometimes, the best way to get what you want (if you’re a criminal) is to simply steal it. In a networking/computing sense this could mean:
- Tapping a connection
- Plugging into a network and monitoring traffic
- Intercepting wireless traffic
- Physically stealing storage devices such as USB Memory Sticks
- Physically stealing a machine such as a laptop or tablet
- Old fashioned printing out of sensitive data!
There is little that can be done to stop most interception or theft and the only real way of protecting yourself and your data is to ensure that all data and devices are using strong encryption and strong passwords meaning data or devices should be useless if stolen.
SQL Injection

What is it?
SQL injection is where an attacker sends an SQL query (a piece of code designed to run on a database) through a form on a website in the hope that it is executed by the web server to perform an action on the database, granting access or deleting data.
Virtually all websites are connected to some form of database which holds all the content, data about users, products and so forth. Web servers are responsible for processing the code in web pages which connects to these databases, retrieve the relevant data and plug it in to the correct place on each page before sending it to a user.
The language we use to communicate with databases is called “SQL” or Structured Query Language. Some clever people realised that when you enter data into a web form or website you are creating an SQL query and could bolt on some SQL of your own to do damage or gain access to a system.
How does it work?
- A malicious SQL query is created which will carry out one of the following:
- Delete a table or some data from a table
- Create a new user, usually an administrator in a table
- Change or amend data
- This query is entered into a web form with the intention of modifying the SQL statement that will be executed on the server.
What does it do?
- Once submitted, the malformed SQL statement will be executed by the server if it does not have the relevant security updates or validation code which prevent that specific attack.
- Once executed, it is likely a hacker would have unauthorised access to a system, have deleted data or inserted new data to gain access/modify a system
How can you protect yourself?
- Have validation on user input – in other words all input must adhere to a set of rules. Anything that does not is rejected.
- Use only stored statements or queries to restrict the possible queries that could be executed by the server to protect sensitive data
- Use penetration testing (see the next section) to deliberately test the security of your website/server.