1.5.2 – Utility Software
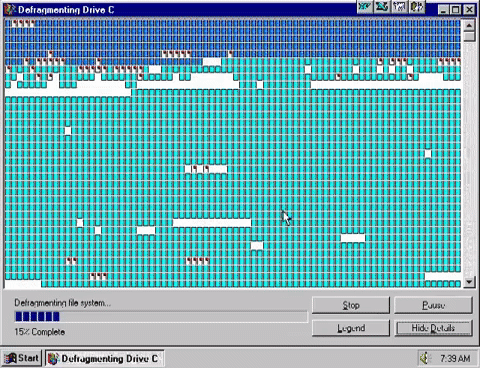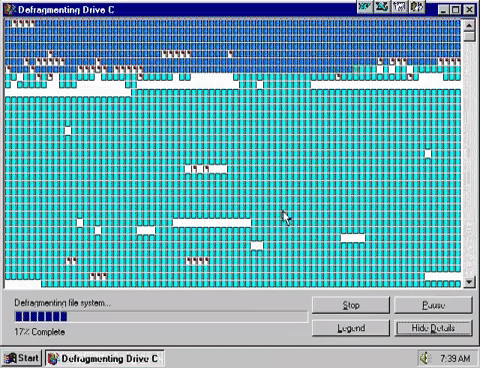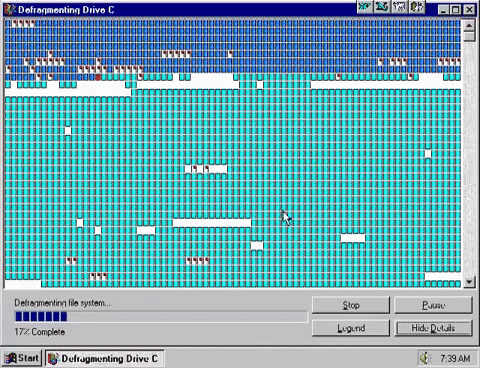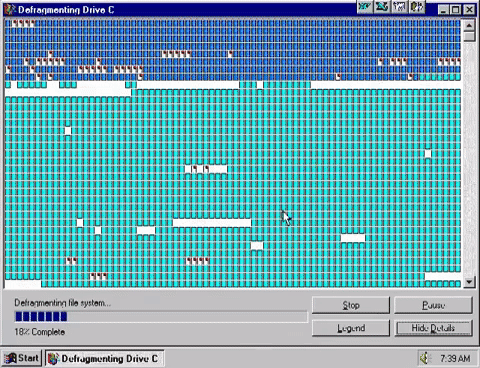
Utilities are pieces of software which perform a single, specific task in a computer system and usually do so in the background with little or […]

Utilities are pieces of software which perform a single, specific task in a computer system and usually do so in the background with little or […]
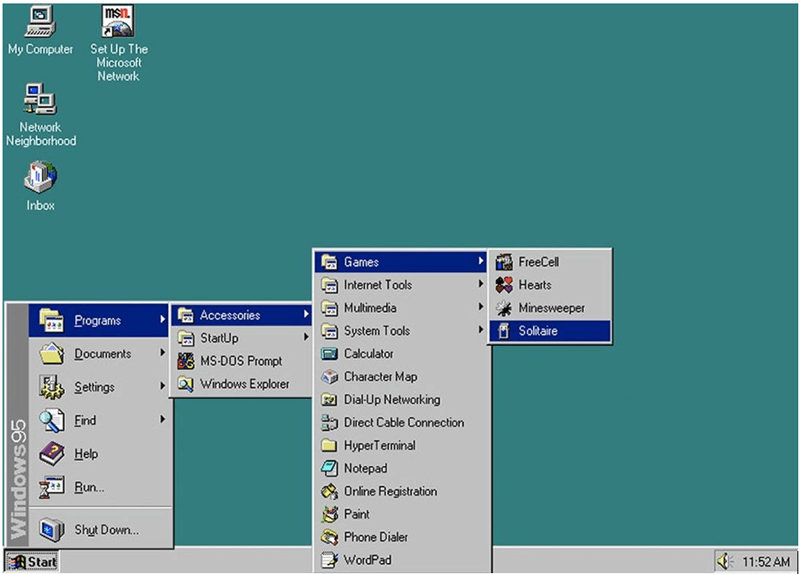
Operating Systems are the single most important piece of software on any computer system. All computer systems must have an operating system in order to […]
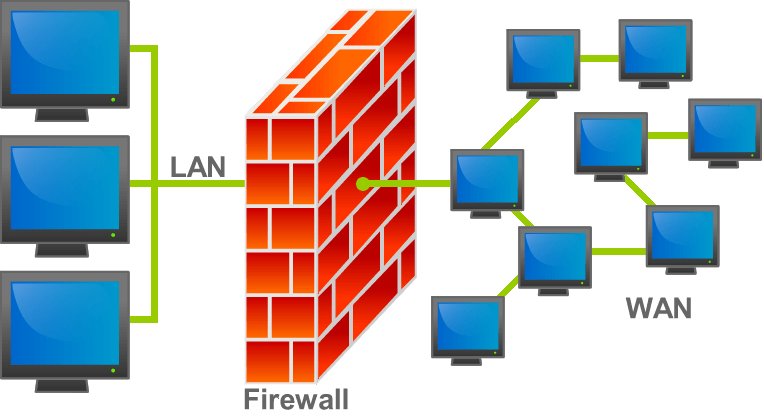
In the previous section, 1.4.1 – Threats to Computer Systems and Networks, we looked at a fairly comprehensive rundown of the most common and prevalent […]

As the number of network connected devices increases, so does the proportion of poorly designed and insecure devices. Many people do not understand the significance […]

In the last section we focussed on what networks are, why they are used and covered a broad range of related topics such as how […]
In this section (click to jump): Performance Factors People that look after networks are odd people. I once convinced a student that every network had […]

Today, our world is connected in ways which were unimaginable a generation ago. We take for granted the ability to communicate in real time, across […]
Compression is all about making things smaller and take up less space. The need to make things take up less space is certainly not unique […]

I am beginning to make progress on recreating the base revision resources that this site used to contain a year or two back. To summarise, […]
The final stop on our encoding journey is sound. In this section we learn how sound waves are translated into a digital, binary form and […]
Copyright © 2024 | WordPress Theme by MH Themes